With Windows 10 now into its latest edition, the 1607 “Anniversary” update, it now appears, for better or worse, to be here to stay. It has generated a lot of interest; supposedly the “last version of Windows”, many expected it to be akin to Windows 7 – an improvement following a much-maligned previous Windows version. However, the reality has turned out to be somewhat different from what many were expecting.
Microsoft are now “cloud first, mobile first”, and a lot of this new strategy shows through – sometimes somewhat cynically – in Windows 10. For my sins, I’ve been involved in a Windows 10 deployment since August of 2015, so now, just over a year in, it is maybe time to share the things I’ve learned in the hope that it may give some of you a bit of help when it comes to deploying (or not deploying!) this new version of Microsoft’s flagship operating system.
This set of articles is going to expand at the rate of one a day over the next week or so, and cover a wide range of issues for those of you deploying Windows 10 – whether it be fully virtualized via Citrix XenDesktop or the like, or simply a general physical deployment. Hopefully, it will be everything you need to know!
You can read the earlier parts of this series from the following links – EDITIONS, SERVICING BRANCHES and MODERN APPS.
TELEMETRY
I already wrote an article about the telemetry side of Windows 10 late last year, so this article may cover a lot of the same ground. However, in the interests of completeness I’ve put this one together, and attacked it from a more neutral perspective, tooling-wise, than the previous article. Also, there are now many more GPO settings available to manage Windows 10 settings, and these have been factored in.
Anyway – what about that lovely word, telemetry? A fantastic euphemism for logging, monitoring, or just downright spying. But – only the most naive amongst us believed that with Windows 10 being free for most users, there wouldn’t be a tried-and-tested attempt at monetization baked into it somewhere. What gets my goat, though, is that the paid-for Enterprise version ships with the same spying features built-in and active. Without even getting into discussions about privacy, security and protection of intellectual property and company data, we all know the score with Windows 10 telemetry – it’s gotta go!
Also, reducing the active telemetry cuts down on the amount of network traffic and attack surface exhibited by a standard Windows 10 system, so getting rid of it is good on a number of levels. Ideally, as much of it as possible should be turned off both in the base image and via automated policies.
PREPARATION
First of all, you need to make sure of a few things to enable you to deal with telemetry settings effectively.
Use Enterprise edition – without it, the telemetry settings can’t be disabled via policy.
Get rid of the Modern Apps you don’t need – Modern Apps like to talk back to their creators, especially the free ones
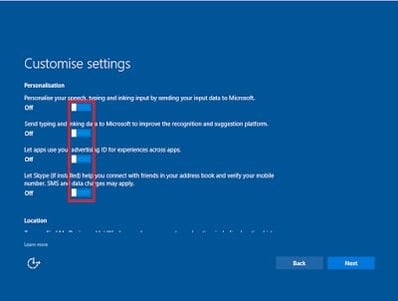
In your base image customization, make sure you de-selected all of the options with regard to telemetry (see image). You may need to set these options to run unattended depending on your imaging technique. We will turn most of them off via the GPO method anyway, but I prefer to have them disabled in the image too in case anything temporarily escapes from GPO management (me, paranoid much?)
Make sure you have a Windows 10 machine with the RSAT (Remote Server Admin Tools) installed so you can access all of the latest GPOs via GPMC. If you encounter problems installing the tools, it’s probably related to this issue with language packs.
Once all of this is done, we can move on to deploying the required anti-telemetry settings.
DEPLOYMENT
Previously I recommended using something like AppSense because the Registry keys for a lot of these settings weren’t applicable by GPO, and had to be layered in after the user had logged on to avoid them being overwritten by the default user profile. However, we can now handle most of them via Group Policy Objects.
The GPO we have configured and made available for download covers Windows 10 GPOs, some extraneous Registry values, and system services associated with telemetry. After that we go into detail about Scheduled Tasks and domain blocks, these parts you would have to configure separately. You MUST test this thoroughly before deploying into your own environments because I’m not being held responsible for anything you break by pushing it out without the required due diligence. If you do break anything and you want my help to fix it, you may well end up paying my full day rate to do so. You have been duly warned!
The GPO with all of the Telemetry settings is available here. It contains, as of the 1607 build available at time of publication, all of the policies that we have identified as being associated with telemetry. Test, test and test again before deploying!
On a system service level, this GPO disables the following services:-
Connected User Experiences and Telemetry (diagtrack)
Data Collection Publishing Service (DcpSvc)
Diagnostic Policy Service (DPS)
Diagnostic Service Host (WdiServiceHost)
Diagnostic System Host (WdiSystemHost)
dmwappushsvc (dmwappushservice) – (incidentally, this service changed its name from 1511 to 1607 – if you want to disable it on 1511, use the name dmwappushsvc)
Downloaded Maps Manager (MapsBroker)
geolocation Service (lfsvc)
Problem Reports and Solutions Control Panel Support (wercplsupport)
Windows Error Reporting Service (WerSvc)
Windows Push Notifications System Service (WpnService)
On a Scheduled Task level, there are a few telemetry-related tasks trying to run as well. (Actually if you want to get an idea of the sorts of things going on in the background of a modern Windows machine, dig through the Task Scheduler, it’s an eye-opener!) To remove these, don’t do what I did and simply disable the Task Scheduler service – that’s a surefire way to kill a Windows 10 desktop.
You can remove them through PowerShell or batch, setting up a startup script to remove them. I’ve used my old trusty favourite schtasks.exe to do this, as it seems to avoid any issues with elevation like I see when using PowerShell for this. Here’s a copy of my GPO Startup Script (lines may wrap)
@echo off
schtasks /DELETE /TN “\Microsoft\Windows\Customer Experience Improvement Program\Consolidator” /F
schtasks /DELETE /TN “\Microsoft\Windows\Customer Experience Improvement Program\KernelCeipTask” /F
schtasks /DELETE /TN “\Microsoft\Windows\Customer Experience Improvement Program\UsbCeip” /F
schtasks /DELETE /TN “\Microsoft\Windows\Autochk\Proxy” /F
schtasks /DELETE /TN “\Microsoft\Windows\AppID\SmartScreenSpecific” /F
schtasks /DELETE /TN “\Microsoft\Windows\Application Experience\Microsoft Compatibility Appraiser” /F
schtasks /DELETE /TN “\Microsoft\Windows\Application Experience\ProgramDataUpdater” /F
schtasks /DELETE /TN “\Microsoft\Windows\DiskDiagnostic\Microsoft-Windows-DiskDiagnosticDataCollector” /F
schtasks /DELETE /TN “\Microsoft\Windows\NetTrace\GatherNetworkInfo” /F
schtasks /DELETE /TN “\Microsoft\Windows\WindowsUpdate\Automatic App Update” /F
As I said, pick whichever method seems to work best for you. The Startup Script isn’t in the GPO I’ve made available for download, obviously because it references paths that you won’t have 🙂
Finally, if you’re really batshit paranoid, any amount of Wiresharking can reveal a bunch of Microsoft-owned IP ranges that Windows 10 likes to talk to on a regular basis. I wouldn’t particularly recommend screwing around with this, as you may cut off access to Office Online or Windows Update or any amount of under-the-hood things, but if you’re really privacy obsessed you can block or null-route these domains using a hosts file or firewall.
 |
| “Block at firewall!” |
Here’s the list (based on my own testing – this may need updating). Given that I don’t recommend doing this, they’re not part of the GPO.
vortex.data.microsoft.com
telecommand.telemetry.microsoft.com
telecommand.telemetry.microsoft.com.nsatc.net
oca.telemetry.microsoft.com
oca.telemetry.microsoft.com.nsatc.net
watson.telemetry.microsoft.com
watson.telemetry.microsoft.com.nsatc.net
redir.metaservices.microsoft.com
choice.microsoft.com
choice.microsoft.com.nsatc.net
df.telemetry.microsoft.com
reports.wes.df.telemetry.microsoft.com
wes.df.telemetry.microsoft.com
services.wes.df.telemetry.microsoft.com
sqm.df.telemetry.microsoft.com
telemetry.microsoft.com
watson.ppe.telemetry.microsoft.com
telemetry.appex.bing.net
telemetry.urs.microsoft.com
telemetry.appex.bing.net:443
settings-sandbox.data.microsoft.com
vortex-sandbox.data.microsoft.com
survey.watson.microsoft.com
watson.live.com
watson.microsoft.com
statsfe2.ws.microsoft.com
corpext.msitadfs.glbdns2.microsoft.com
compatexchange.cloudapp.net
cs1.wpc.v0cdn.net
a-0001.a-msedge.net
statsfe2.update.microsoft.com.akadns.net
diagnostics.support.microsoft.com
corp.sts.microsoft.com
statsfe1.ws.microsoft.com
pre.footprintpredict.com
i1.services.social.microsoft.com
i1.services.social.microsoft.com.nsatc.net
feedback.windows.com
feedback.microsoft-hohm.com
feedback.search.microsoft.com
bingads.microsoft.com
www.bingads.microsoft.com
apps.microsoft.com
www.apps.microsoft.com
And that just about sums everything up, from a telemetry perspective!
SUMMARY
This isn’t by any means a complete optimization guide – this deals with everything within Windows 10 that relates to telemetry. Whilst removing the telemetry areas is an essential part of optimization, there are other areas that need to be covered to allow Windows 10 to operate optimally. This will be covered further in the Optimization part of this series – provisionally aimed to be part #7.
I would recommend using the GPO I have created, as long as you test thoroughly. If you also use the Scheduled Tasks-killing Startup Script in your environment, pay particular attention to this. In our lab, we didn’t see any instability with all of the tasks removed, but we operate on a small application set (Office 2016, Adobe Reader and Chrome), so you need to do proper testing before inserting that startup script into a live environment.
The blocking of domains I would, personally, leave well alone. Aside from the fact you will have to constantly maintain the list, you also may break parts of the operating system or applications set.
But hopefully, this should provide a good baseline for thoroughly disabling telemetry on your Windows 10 systems. Just ensure that you keep an eye on updates and rollups to ensure they don’t change the policies or Registry keys you are using to disable this. In fact, an important part of Windows 10 change process will end up being the validation of existing policies and configurations against new servicing updates and feature upgrades, in order to ensure the goalposts haven’t moved. I can barely conceal my excitement at the prospect of this!
Stay tuned for part #5 of this series, which, all things going to plan, should be on the lovely subject of THE START MENU.